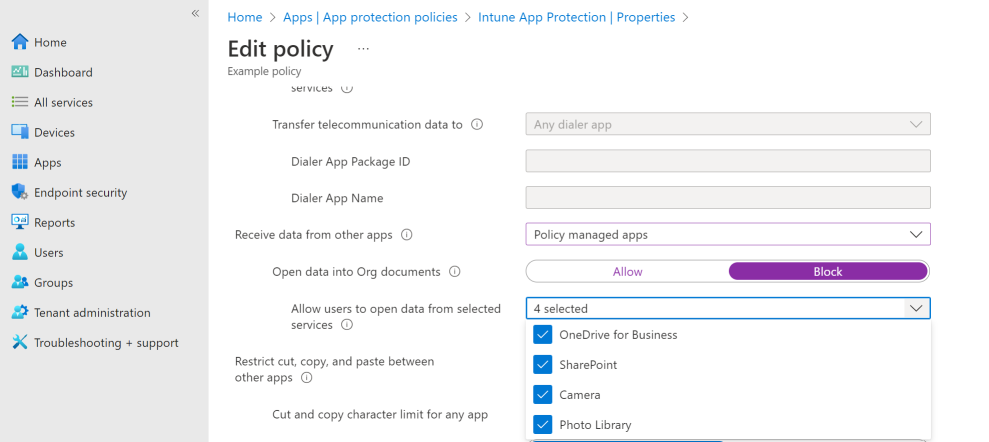
This article gives troubleshooting guidance for common scenarios in which data transfer isn't restricted as expected with Intune app protection policies (APP). For general troubleshooting guidance related to data transfer and Intune APP, see Troubleshooting data transfer between apps.
In this scenario, a user can't transfer corporate files between managed apps or copy and paste data from a corporate document to a managed app.
In this scenario, a user can't receive files from unmanaged apps. For example, files can't be inserted into a document from the Camera, OneDrive for Business, or SharePoint app.

In this scenario, a user needs to transfer files to unmanaged apps even though you have set Send org data to other apps to Policy managed apps.
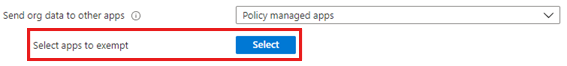
In this scenario, a user can't save files to local storage. Typically, this occurs because either (or both) of the settings below are configured.
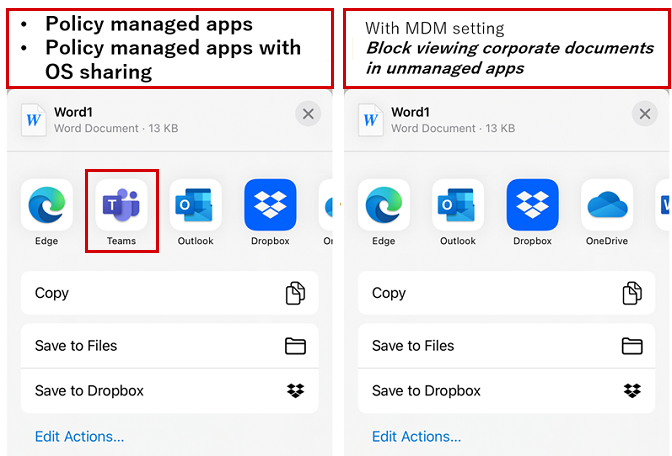
Oftentimes, admins want to filter the list of apps displayed in the iOS Share extension (receiving apps) to prevent data transfer to unmanaged apps. There are two methods to control which apps are available in the Share extension. You can combine both methods if you're using an Mobile Device Management (MDM) solution.
With this configuration, if the sender app is MDM managed, only managed apps will display in the sharing extension. In the example below, the Teams app isn't deployed with Intune, so the app isn't displayed in the Share extension.
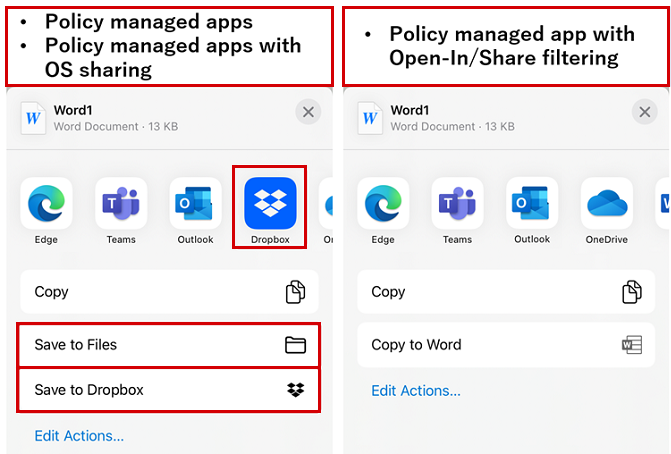
With this configuration, the share extension is filtered to show only apps that support Intune APP. This method can be used for an Application management without enrollment scenario. The following example shows how available apps in the share extension will change once the policy is set to Policy managed app with Open-In/Share filtering. In this example, the Dropbox app isn't displayed in the share extension because it doesn't support Intune APP. Also, the Save to Files option is filtered out to prevent data transfer using the local Files app.
On Android work profile and fully managed devices, there are some considerations for controlling which apps your users can share files to (receiving apps). Use managed Google Play to deploy the apps you want to allow data sharing between. Don't deploy other unnecessary apps. For Android work profile devices, users can share files only between apps installed in the work profile.
If the Microsoft Edge app is not installed on your device, clicking on URLs from policy managed apps won't work. In the case of Android Enterprise WorkProfile scenarios, the app needs to be installed in the WorkProfile region on the device. If the Microsoft Edge app is not present, you will see an error message indicating your organization requires the application to view the link.

